If you're reading this article, you probably know that Mac OS X has a built-in firewall that should be turned on at all times. But how do you know that the firewall working, and how do you find out what's happening behind the scenes? To check, you need to access your Mac's firewall log- a file that contains a record of every event the firewall has processed.
Here's how to monitor your Mac's firewall logs:
- Verify that your Mac's firewall is turned on.
- Open the Console application. (It's in Applications → Utilities.) The window shown below appears.
- In the sidebar, find the
/var/logdirectory. Click the disclosure triangle next to that directory.
- The most recent log entries from the Firewall are stored in the
appfirewall.logfile. Find that file in the sidebar and select it.
- The log entries from the firewall log appear in the right-hand pane of the window. If you scroll all of the way to bottom, you can watch the firewall entries update in real time!
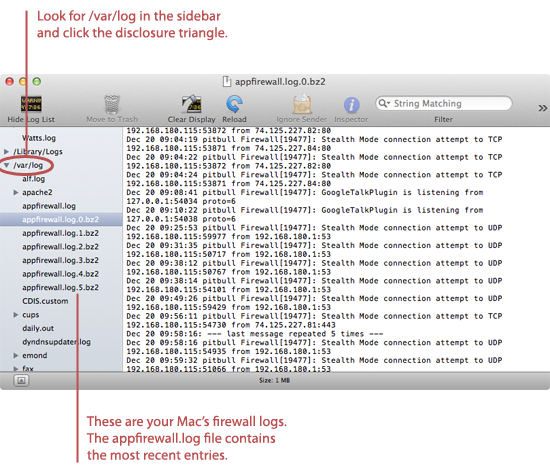
As mentioned earlier, the
appfirewall.log file contains the most recent log entries from the firewall. Once that file fills up with log entries and reaches 1 MB, the log is rotated, and all of the entries in appfirewall.log are moved to appfirewall.log.0.bz2. (And all of the other archived log files are also renamed. For example, the appfirewall.log.0.bz2 file becomesappfirewall.log.1.bz2.) So if you're looking for firewall events that occurred several weeks ago, you'll need to start your search in one of the files with older log entries.How to Read Firewall Log Entries
Unless you have some experience looking at log files, the firewall events probably look like a bunch of mumbo jumbo. Don't worry. Once you understand the basics, you'll be able to discern what's happening with many of the events.
Take a look at the entry below, for example:
Dec 27 21:50:58 Pitbull Firewall[113]: Stealth Mode connection attempt to UDP 192.168.0.2:49747 from 192.168.0.1:53
Here's what each part of the entry means:
Dec 27 21:50:58is the date and time when the event occurred.
Pitbullis the name of the Mac in this example. Your computer's name will be there in its place.
Firewall[113]is the type of log event. (All of the events in this particular log file are firewall events.)
Stealth Mode connection attempt to UDPmeans that another computer on the LAN or WAN attempted to connect to your computer when it wasn't expecting it. UDP is the type of protocol.
192.168.0.2is your Mac's IP address. Since it starts with192.168, we know that this is an internal address on the LAN. And49747is the port on your Mac the other computer attempted to connect to.
192.168.0.1is the IP address of the computer or device attempting to initiate a connection with your Mac. And53is the port that the connection attempt originated from.
Practice makes perfect. After a while, reading your Mac's firewall log will become second nature. You'll be able tell which events are important and which events are benign. More on that in the next section.
Should I Be Concerned?
Most events logged by the firewall are completely harmless. There's no reason to be concerned about 99% of the events in the log, unless you're experiencing connectivity problems on your Mac. In the example above, the firewall blocked valid traffic from a DNS server, which could conceivably cause problems.
When in doubt, search Google for the port the connection attempt originated from and the port on your Mac the other computer tried to connect to. Many times you'll find that the ports are fairly typical and correspond to an application running on your computer. For example, a Torrent server connection might be blocked when you are running an application likeTransmission.
If you see a lot of connection attempts to a lot of different ports, that could be an indication that your computer has been port scanned by another computer - a process that looks for open ports and vulnerabilities. But even if your Mac was port scanned, your Mac's built-in firewall will block it. So again, there's no reason to be concerned.
So the bottom line is that most events in the firewall log are "normal" and indicate that the firewall is working. Don't panic if you see a lot of entries in your logs!
Final Thoughts
Obviously, monitoring the firewall log is not something you need to do regularly, or even occasionally. This is a trick that comes in handy only when you need to verify that the firewall is working, or when you suspect a problem or hacking attempt. Of course, system administratorsroutinely check firewall logs as part of their job duties, but that's in an enterprise environment.
submitted by guest bloger
anita schnide
atlanta, US
Retweet this story
submitted by guest bloger
anita schnide
atlanta, US
No comments:
Post a Comment